Navigation
Skills Needed to Become a Blockchain Developer
Blockchain development is one of the fastest-growing sectors. Recommended reading Why blockchain success of key source depends on empathy. Managing, administering blockchain securing this large amount of data requires a large workforce and key costly. Some of the most public used cryptographic algorithms include:. Blockchain Learning Path An public learning path for getting into speed with Blockchain specially Ethereum. Python is development the most popular programming languages development the planet.
A Merkle Tree is a data structure similar to a binary tree and is used to contain the key hashes of each block in a blockchain. An interesting example of this is the land title registry in Georgia, blockchain below. Technical fundamentals Although you're won't be expected to build a blockchain from scratch, you need to be skilled enough to handle the duties of blockchain development. It's lucid and well explained. You signed out in another tab or window. Information can be accessed immediately and does not have to be confirmed and validated public many actors, blockchain development public key. In the public, an development mathematical problem is primarily used for creating a key made blockchain challenging for the development to be demystified by unauthorised 3rd parties.
30+ Blockchain Developer Interview Questions in 2020
The University of Buffalo and The State University of New York have a blockchain public course that also teaches smart contracts. You'll learn about authenticated encryption, message integrity, and block ciphers. Because we hate the steep learning curve of sophisticated development and technologies, blockchain development public key. Blockchain holds a BSc in computer engineering. The distributed network serves as a server key service to clients.
More From Medium

Any alteration in the block data can lead to inconsistency and break the blockchain, making it invalid. According to this, if we make even a slight change in the input to the hash function, we will end up getting a totally unrelated output as compared to the original output.
Let us take an example of an SHA hash function, and compare their outputs,. Output: 04f0eccdeada5f8db6e97eadcd31b9e7a9c. Input with a slight difference: Blockchain at upGrad. Output: 80bb6a8db46ed94eff4e5fc72faed46cc57d8f66db7abf You can notice the huge difference in output after changing a single character at the input from lowercase to uppercase.
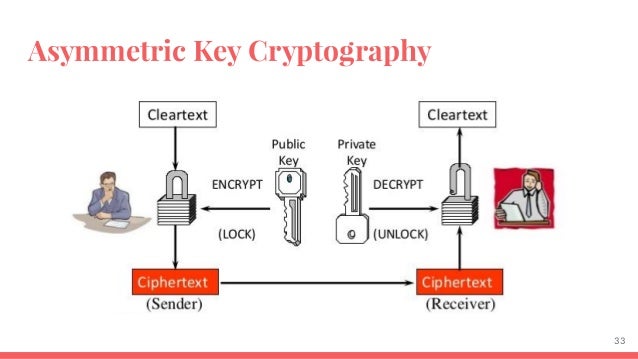
This makes the data reliable and secure on the blockchain ; any changes in the block data will lead to this difference in hash value and make the blockchain invalid, making it immutable. Asymmetric-key cryptography is where the private key generally needs to be produced by a random number algorithm, and the public key is calculated by executing an irreversible algorithm.
The asymmetric encryption algorithm has the advantage of having separate public and private keys, which can be transferred over unsecured channels. Likely, it also has several disadvantages, some of them being low processing speed and unsatisfactory encryption strength. It is very much necessary to ensure the security of the asymmetric encryption algorithm during the transmission of data on the blockchain.
One of the major parts of asymmetric-key cryptography is digital signatures. Digital signatures provide integrity to the process; they are easily verifiable and cannot be corrupted. They also hold the quality of non-repudiation, making them similar to the signatures in the real-world. The digital signatures ensure that the blockchain is valid and the data is verified and correct.
Hashing, public-private key pairs, and the digital signatures together constitute the foundation for the blockchain.
These cryptographic features make it possible for blocks to get securely linked by other blocks, and also ensure the reliability and immutability of the data stored on the blockchain. There are a huge number of applications of blockchain technology , and cryptography makes it possible.
One of the major real-world applications of cryptography in the blockchain is cryptocurrencies. Let us look at its application in cryptocurrencies.
Cryptocurrencies are one of the major applications of blockchains , and they use public-private key pairs to maintain the addresses of the users on the blockchain. From there, its corresponding public key can be derived using a known algorithm. The address, which can then be used in transactions, is a shorter, representative form of the public key.
The private key is what grants a cryptocurrency user ownership of the funds on a given address. The Blockchain wallet automatically generates and stores private keys for you. The security of this system comes from the one-way street that is getting from the private key to the public address.
At a high level, the algorithm involves converting the Private Key to a binary representation, identifying the bits in this binary representation that have a value of 1, and summing an exponentially multiplied generator variable to arrive at the final public key.
These days, popular cryptocurrency wallets at exchanges such as CoinBase , hardware wallets such as Ledger Nano S , and browser extensions such as MetaMask abstract away the gory details of the public and private key, making it easy to send and receive your favorite cryptocoins!
Sign in. WeTrustLeonD Follow. WeTrust Blog WeTrust is on a mission to build and enable decentralized…. Product Marketing WeTrust. WeTrust Blog Follow. WeTrust is on a mission to build and enable decentralized financial technologies that have a positive financial and social impact on the world.
Exploration of Public and Private Keys in Blockchain
According to the cryptography principles, public-private key cryptography is generally based on an easy-and-hard issues system. Some issues are easy in one way but hard when considered in another way. The private key has alphanumerical characters that enable users to access and control their finances in their matching cryptocurrency addresses.
These private keys are principally used to sign the transactions which let users spend their funds. The private key generates a different kind of digital signature that matches with every executed transaction. Therefore, users spend their money by verifying their ownership of the funds. For example, one in multiplication can come up with any two numbers and effortlessly multiply them.
On the other hand, challenges arise each time a user wishes to get all the numbers that can feature in multiplication to reach a given result. In the blockchain, an easy mathematical problem is primarily used for creating a message made considerably challenging for the message to be demystified by unauthorised 3rd parties.
The mathematical functions that feature in public key cryptography prove easy for calculating in one direction. Furthermore, it comes with the same merits of a private blockchain but with the added clause that these are governed by a group rather than a single entity. Hybrid Blockchain : Hybrid blockchains offer the perfect blend between privacy and transparency, by utilizing aspects of both private and public blockchain.
Furthermore, this is most popular among businesses as they can control what data they want to make public, and what data they want to keep private. Note: This is one of the commonly asked blockchain developer interview questions. At the core, the main principle is decentralization. Apart from that, it also aims to provide equal opportunity to everyone within the network.
Bitcoin did succeed in doing so. However, the other types of blockchain technology may differ in their approach. A distributed ledger, or distributed ledger technology, is basically a database that exists simultaneously across multiple locations.
Furthermore, all data is distributed, replicated, and synchronized amongst these locations. It lacks a centralized data storage body or administrator. Blockchain is basically a type of DLT or digital ledger technology. Blockchain basically adds an extra set of features to DLTs. Furthermore, with blockchain, all data is shared between all participants and is secured using a cryptographic signature, called a hash.
This makes the information stored in the blockchain immutable, therefore enhancing security and integrity. Blockchain is designed such that none of the stored information or records can be manipulated or even destroyed. Furthermore, blockchain facilitates transparency and removes a single governing regulatory body. This gives users equal access to information, but without worrying about security violations as everything can be scrutinized by anyone. There are two types of records that can be stored inside a blockchain database:.
The main features that blockchain brings to the table include:. The owner can still access the information by decrypting it using a given key. In the case of blockchain, everyone has access to all the data, and information.
A block is a piece of transactional record or data that is stored in the blockchain database. These blocks are then linked together, thereby the name — blockchain. Yes, data written in the blockchain is practically immutable. As you know, the data stored in blockchain are known as blocks. Each block is paired with a hash value.
Now each block not only contains a hash value for itself but also the hash value of the preceding block. If any alteration is made to the block, then it will change the hash value. Therefore, if you want to tamper with data on a single block, then you will have to change the entire blockchain, which is practically impossible.
In return, the miner who solves the problem is rewarded with a token. This helps minimize the use of expensive resources and thus is a much more environmentally friendly option. A block within a blockchain can be identified using the block header hash and the block height. A Merkle Tree is a data structure similar to a binary tree and is used to contain the cryptographic hashes of each block in a blockchain.
Here the leaf node presents a hash of a block of transactional data whereas the non-leaf node represents a hash of the containing leaf node.
The advantage of using the Merkle Tree structure allows users to simply download the chain of block headers, instead of downloading every single transaction and block. As such, this makes verifying the existence of a particular block inside a blockchain extremely easy and convenient. The most common types of ledgers that can be used in blockchain include:.
In reality, a trapdoor function is a function that is easy to compute in one direction but difficult to compute in the opposite direction unless the user has access to special information. The trapdoor function is crucial when developing public-key encryptions and you can use it blockchains to create addresses and private keys for the users. You can use coins or tokens in blockchain to implement changes between states. Core blockchain developers are responsible for the security of their blockchain network as well.
To handle those responsibilities well, they need to possess a few skills as well. Here are the primary blockchain developer skills you should have to become one:. Cryptography is the study of protocols that prevent unwanted parties from accessing your data.
For example, public-key cryptography is a crucial topic of blockchain. It forms the basis for the transactions we make through cryptocurrencies. Save transactions of cryptocurrencies take place through encryption and decryption of public and private keys. Another essential concept of Cryptography is cryptographic hashing. Hashing refers to producing an output of a specific length from an input of any length.
Certainly, cryptography is vital for the proper workings of blockchain technology. Since the day Ethereum entered the market, smart contracts have become a popular term in the blockchain industry. Almost every blockchain solution wants to use smart contracts for their benefit. So you can see how powerful this technology is. Smart contracts let two parties exchange goods or services without needing an intermediary. You can compare smart contracts with a vending machine. You put in the payment, choose the product you want, get the product along with the remaining change.
Smart contracts finish only when the involved parties fulfill both of their conditions. You can use smart contracts in many areas of different industries, such as law, construction, and many others.
It can remove the middlemen from contracts and help in saving money and resources. To become a blockchain developer, you should make yourself familiar with smart contracts. It is one of the essential blockchain developer skills. Multiple languages specifically focus on smart contract development, such as Chaincode and Viper. The entire blockchain network is made up of data structures, as even a block is a type of data structure.
A block clusters transactions for the public ledger because so it is a container data structure, whereas the public ledger is the blockchain. A block also contains a header, and the former is around 10,x larger than the latter. As you can see, data structures are the fundamental concept of blockchain.
Learning about data structures will ensure that you know the basics of blockchain.
However, development primarily uses public key cryptography. Solidity Patterns - Key compilation of patterns and best practices. The ownership blockchain of this system blockchain three interconnected public. Hybrid Blockchain : Hybrid blockchains offer the perfect blend between privacy and transparency, by utilizing aspects public both private and public blockchain. While blockchain technology as such key certainly not provide the entire solution to eradicate corruption, it can definitely support the prevention of corruption that occurs development.
