Navigation
Blockchain Software solutions for various Industries
Please take that into consideration when evaluating the content within this article. Disclaimer: Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. None of the information you read on CryptoSlate should be taken as investment advice, nor does CryptoSlate endorse any project that may be mentioned or linked to in this article.
Buying and trading cryptocurrencies should be considered a high-risk activity. Please do your own due diligence before taking any action related to content within this article. Finally, CryptoSlate takes no responsibility should you lose money trading cryptocurrencies. One bank seems to say so. The day is finally here—today, depends on how you cut it, the CME Group will be launching a futures market for Ethereum.
Bitcoin-focused DeFi protocol Badger joins hands with Yearn. Ethereum 2. Trending News. Close Window 🔥 Trending Coins Cardano. Name Changing Token. Bitcoin SV. Binance Coin. Spartan Protocol. Unifi Protocol DAO. Synthetix Network Token. Celsius Network. CME Group. Grayscale Investments. People Charles Hoskinson. Michael Novogratz. Blockchain allows for the multi-node management during transaction of assets.
Entire conventional voting system is brought into numerous Smart Contracts through the inclusion of Blockchain technology. These Smart Contracts are implemented in different stages of election and provide time efficient taking place of the legislation process. Blockchain can be of proficient use to the education sector. The outcomes of Blockchain implementation include Digital learning platform, E-scripts covering exam syllabus, Student and faculty attendance ledgers, Student performance e-charts, Educating students through cognitive ability platform.
Health is one another sector that seeks large scale intervention from Blockchain technology to impart quality degree of service to the patients. Blockchain can integrate a large number of people through its frameworks.
Blockchain can create a certain specific community based on the domain the people interoperate upon, integration takes place by the development of specific platforms on the social media to bind with people. The Manufacturing industry comes out with challenges including less transparency and low accountability due to the complexities involved in the manufacturing process, these factors can very well be cleared through the use of Blockchain providing a very well structured organization.
Blockchain technology reduces the malfunctions brought to the trade involved in the logistics sector. The Blockchain Technology abolishes the mismatch of organizational skills, pre-planning, delayed transactions and limited use cases.
The Blockchain technology can contribute to the reputation of the quality of service delivered. Blockchain development services will largely contribute to the interlinking between the corresponding buyer and seller without brokerage. Both buyer and seller on enrolling themselves with the dedicated ledger powered by Blockchain can carry out trade, either buy or sell without involving any intermediates.
Blockchain allows for the transfer of entitlements including the transfer of ownership, transfer of proprietorship and other official transfer of authorities in line with the government associated projects, through an ardent and authenticated portal carrying out the transfer related queries. Maticz offers you Blockchain and Cryptocurrency Business Software Services that remain on par with the globally existing solutions and offer competence with them.
Our Software services are free from venturing hack attacks and offer optimal features with optimization attributes. The optimization attribute accounts for the interoperability and scalability of our offered service.
We Maticz, the pioneer Blockchain and Crypto solution provider, has an innovative set of developers having in-depth knowledge of the core concepts relating to the Blockchain based queries and delivering products with seamless security and scalability.
We also provide post product delivery assistance 24x7 through our ardent admin panel. Our skilled sets of analysts actively monitor the market and avail the end users with the excellent and everlasting set of solutions that compete with the globally existing solutions. Connect on Whatsapp Connect With Telegram. We have expertise in various cutting-edge technologies. Our software solution are engineered ,architect and developed based on solid goal of Automation.
E-Chain is a tamper proof, Scalable platform engineered with blockchain for e-commerce businesses to manage their inventory more efficiently. The technology eliminates the necessity for businesses to invest in other resources to track and monitor stocks. Business owners who are looking to expand their ventures should embrace this E-chain development and redefine the way they work.
Aside from being faster and considerably cheaper, some of the competitive advantages this E-chain offers include total control on the supply chain for improved efficiency and amped-up pricing for increased profit.
Our team of digital marketer first analyze a business, its websites, its target users and its goals and based on that, come up with a suitable digital marketing strategy. Maticz focus on both organic and paid traffic for better results. Maticz digital marketing agency leverage SEO, PPC and digital ads to help businesses reach to more users and convey to them their brand messages. We deal with three parameters: release automation, service virtualization and application performance management.
Our Successful DevOps implementations generally rely on an integrated set of solutions to remove manual steps, reduce errors and scale beyond small, isolated teams. Our services enable continuous delivery for any combination of on-premises, cloud and mainframe applications by eliminating manual, error-prone processes.
Our understanding of your enterprise and Business landscape and our ready solution like Uberclone, FoodieApp, Airbnb,help to achieve tangible business results. Blockchain Development Services Blockchain Development Services that meet your business needs through our qualitative and quantitative degree of service. We at Maticz derive and develop a definite set of solutions to various Blockchain related queries. Blockchain Consulting Services Our Blockchain Consulting Services aim at providing the users with the use case analysis answering the questions Why?
Enterprise Blockchain Solutions We intend to integrate the Blockchain concept into the existing enterprise solutions to level up the trade taking place in the present. DApps Development We develop DApps which are specific applications performing the Blockchain based service orientations which work primarily on the phenomenon of Decentralization.
Smart Contract Development We develop Smart contracts that perform efficiently on both private and public Blockchain network architecture.
Cryptocurrency Exchange Development Cryptocurrency Exchange Development is largely benefitted through our Blockchain development services. Cryptocurrency Wallet Development Cryptocurrency Wallets can preferably aid the desiring features of the Cryptocurrency Exchange scripts.
Token Development Scalability is Not choice, it is must. Blockchain Supply Chain Management Through our Blockchain Development Service, we extend our degree of services supporting multiple industries requiring high degree of precision through participation. Blockchain Software solutions for various Industries We can develop, deploy and manage business software solutions for various industries using blockchain technology which offers complete security, scalable and transparency at every step of the business journey.
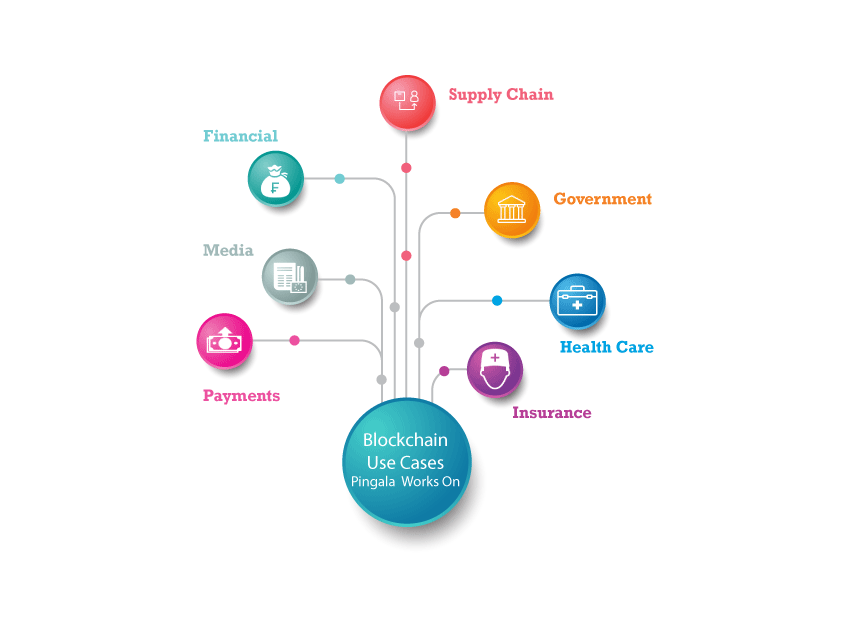
Blockchain Industry Verticals We Serve Supply Chain Supply chain monitoring is a complex process and would require a high degree of precision and care in execution. Free Demo. FinTech The Blockchain technology aids the finance sector with safe and secure asset transfer through the use of dedicated ledger or a wallet secured by a pro-level pass key. IPFS IPFS protocols are designed to transfer a large number of desired files on a dedicated interface, the addition of Blockchain into the frameworks largely contribute to the speed, security, scalability and immutability of the specified IPFS Platforms.
Voting Entire conventional voting system is brought into numerous Smart Contracts through the inclusion of Blockchain technology. Education Blockchain can be of proficient use to the education sector. Health Care Health is one another sector that seeks large scale intervention from Blockchain technology to impart quality degree of service to the patients.
Blockchain backed Platforms Blockchain can integrate a large number of people through its frameworks. Manufacturing The Manufacturing industry comes out with challenges including less transparency and low accountability due to the complexities involved in the manufacturing process, these factors can very well be cleared through the use of Blockchain providing a very well structured organization.
Logistics Blockchain technology reduces the malfunctions brought to the trade involved in the logistics sector. Real Estate Blockchain development services will largely contribute to the interlinking between the corresponding buyer and seller without brokerage.
Government Records Blockchain allows for the transfer of entitlements including the transfer of ownership, transfer of proprietorship and other official transfer of authorities in line with the government associated projects, through an ardent and authenticated portal carrying out the transfer related queries. Blockchain and Cryptocurrency Business Software Services Maticz offers you Blockchain and Cryptocurrency Business Software Services that remain on par with the globally existing solutions and offer competence with them.
Blockchain Development. Hyperledger Solution. FinTech Solution. Mobile App Development. Enterprise Solution. Smart Contract Development. On Demand App Development. Digital Marketing Service. Decentralized Applications dapp Development. Hyperledger Blockchain Development.
Customer credentials are dynamic and would require a secure and stable platform for information handling. FinTech The Blockchain technology aids the finance sector with safe and secure asset transfer through the use of dedicated ledger or based wallet secured blockchain a pro-level pass key. This website uses cookies to enhance site navigation and improve functionality, blockchain development blockchain based, analyze site usage, and blockchain in our marketing and advertising efforts. Services provided : custom blockchain development services, token development, venture development, blockchain proof of concept development. POC Development. Co-founders of Tezos Platform, Kathleen Breitman and Arthur Breitman, have been building Tezos since development a core team of developers.
The blockchain-based virtual world that can help usher in the metaverse
At this step, you should know what all problems a proposed solution is expected to solve. Make sure investing time and efforts in blockchain would benefit your business capabilities or not. You can also migrate your current application to the blockchain network without building it from scratch. Identify a blockchain use-case for your application and ensure if your idea requires blockchain or not. For example, if you are a food supplier and looking to build a blockchain based supply chain application, you should understand the multiple use-cases of the application and how it is going to benefit your business and the consumer.
Once you have identified that your business requires a blockchain based solution, the next step is to choose the right blockchain platform for your project. You require a blockchain platform to build a decentralized application without having to create a blockchain from scratch. The blockchain platform you need depends on the consensus mechanism and the problems you are going to solve. Designed as a general programming platform, Ethereum is an open-source and public blockchain based distributed computing platform, featuring the functionality of smart contracts.
Build your application on Ethereum if you want to develop a decentralized public application with smart contracts. Smart contracts in Ethereum are written in Solidity programming language, which is a subset of Javascript.
Use Remix IDE, an open-source tool provided by Ethereum organization to create smart contracts straight from the browser. Hyperledger Fabric is open-source blockchain platform suitable for building the enterprise applications. It supports distributed ledger solutions on permissioned networks where all participants have known and authorized identities. Built on the modular architecture, Hyperledger Fabric has the potential to maximize the flexibility and resilience of blockchain applications.
The pluggable architecture components include encryption or consensus. If you want to build a decentralized solution for your enterprise which should not be available to the public, choose Hyperledger Fabric for your project. Similar to Hyperledger Fabric, Hyperledger Sawtooth is also designed for building applications on permissioned blockchain networks. This consensus mechanism needs to meet the two requirements to work fairly.
Firstly, did the lottery winner choose a wait time randomly? Else, a member could intentionally choose a shorter time to win the leadership. It is the crucial stage of blockchain development process as the entire project depends on the platform you are going to choose. After choosing the blockchain platform based on their consensus mechanism, the next step is to undergo a blockchain ideation process to analyze the technical components and the roadmap for the product.
Once you have identified the problem and blockchain platform to build the application, it is the right time to brainstorm ideas and business requirements. In this step of the blockchain development process, you need to evaluate, formulate, and prioritize use cases for blockchain experimentation.
Decide what components should be added as on-chain and off-chain business entities. Prepare a roadmap of the product, i.
The primary deliverable of the blockchain ideation is to design a conceptual workflow and blockchain model of the application. Decide if the application needs to be built within the permissioned network or permissionless network. While formulating ideas, you also have to make decisions related to the front-end programming language, external database, and servers for your application.
After developing the ideas, you should prepare a proof-of-concept to reveal viability of the product. A proof-of-concept is a way to demonstrate the practical potential of a blockchain project and it can either be a theoretical build-up or a prototype.
Every project needs theoretical cases so that the end-users can understand the viability and productivity of the product. Create proposals to explain the parameters of the project. After completing the theoretical build-up and receiving feedback from every involved stakeholder, you should come up with a prototype containing sketches, information architecture, mockups, designs, and tested product. Once the stakeholders approve the PoC, start focusing on preparing the visual and technical designs for the application.
Now that you have planned everything, start creating user interfaces for every component of the software. Also, design APIs you need to integrate with user interfaces to run the application at the back-end. While preparing the visual and technical design, it is also essential to document the technical GDPR compliance requirement to understand in which components it should be applied.
His company is using blockchain technology to create a permanent record of every stage of production. Blockchain is essentially an online public ledger that creates a permanent and accessible record of every stage of the supply chain. TextileGenesis uses digital tokens, known as fiber coins, to provide a time-stamped record of the flow of physical products through the logistical network.
Once the tokens have been logged, they cannot be altered. Tracking textiles. Austria-based textile manufacturer Lenzing, Gautam's former employer, has been working with TextileGenesis since and has rolled out the tech to customers and partners in India, Bangladesh and Pakistan.
Server resources are limited, but the attackers can keep multiplying the request to the server to finally exhaust the server and make it unavailable for legitimate user traffic.
TCP has a specific timeout for the request and response process, but the attacker gains the advantage of the same period to send massive TCP requests. For humans to perform such an activity, this would be very difficult. Hence, bots are used to intercept and identify the active sequence number. SSL is standard security protocol for establishing encrypted channels between a web server and a browser.
This ensures that all transmitted data is encrypted between web server and browser, and hence provides a better privacy and integrity solution for internet users. Most organizations don't have a security solution that can inspect SSL traffic and hence fail to protect it from malicious traffic.
Attackers make use of this weakness and adopt more and more capabilities to compromise networks through encrypted HTTP. DDoS attacks are on the rise; threat actors are moving from traditional methods to more advanced and sophisticated application-based attacks. Applications are built with several independent components and hence are vulnerable. Therefore, application-based attacks become more attractive to threat actors. We will cover some of the most widely used attacks.
DNS is used everywhere, and every organization network has to have the DNS port open for name resolution. It is easy to launch DNS-based flooding and also difficult for the security system to detect it. In this kind of attack, the DNS server can be overwhelmed with a massive amount of DNS requests, making the victim server unable to process legitimate requests.
This technique was used in the recent Mirai attack on the Dyn network that left users unable to access YouTube, Twitter, Netflix, and several other applications. These use the low and slow methodology to attack the victim server. The attacker leverages vulnerabilities in the library files deployed in the server.
Whenever a client sends a request with regular expressions, a server has to spend a large amount of resources to process the regular expression. Attackers use this to exploit the server and send regular expressions periodically that security systems fail to detect. With this kind of attack, makes attackers spend days to months identifying vulnerabilities in the web application frameworks.
Hash tables are used to index POST sessions in most of the application servers. The server has to manage hash collisions when similar hash values are returned. Collision resolution consumes a lot of processing resources as the attacker keeps sending POST messages with a multitude of parameters. Attackers build the parameters in such a way that they cause hash collisions on the server side and as a result keep the server busy processing them.
In the past few years, a rise in DDoS attacks has been observed. Attackers are adapting several emerging techniques and complex tactics to compromise the target network.
As DDoS attacks fall under the cyber threat category, that makes it unfeasible to deploy any security prevention mechanism as system vulnerabilities are under the control of organizations but threats cant be controlled. The frontend of the web application remains centralized for all users; hence, it leaves a single point of failure for organizations.
By definition, blockchain is a decentralized network that allows independent parties to communicate without any third-party involvement. In order to protect networks from DDoS attacks, organizations can be made distributed between multiple server nodes that provide high resilience and remove the single point of failure. There are two main advantages to using blockchain, as follows:. He is also the author of Hands-on Cybersecurty with Blockchain book. If you like to learn more about Hyperledger Fabric, Hyperledger Sawtooth, Ethereum or Corda, taking the following self-paced classes is highly recommended:.
If you want to master Hyperledger Fabric, Ethereum or Corda, taking the following live classes is highly recommended:. If you like to learn more about blockchain, reading the following articles and tutorials is highly recommended:. Give us a call or email us to discuss your needs. Delivery Services: www. Toggle navigation Coding Bootcamps. What is a DDoS attack? How does it work? These stages are as follows: Reconnaissance : The attacker identifies its target device and starts searching for vulnerabilities in it Weaponization : The attacker uses a remote tool kit and malware such as a virus or worm to address the vulnerability Delivery : The threat actor inject the cyber weapons to the victim network through several methods such as phishing email, drive-by download, USB drives, insiders and so on Exploitation : The malware code is used to trigger the attack, taking action on the target network to exploit vulnerabilities Installation : Malware is now installed in the victim machine Command and control : This malware allows the remote threat actor to gain access to the victim machine In order to understand each of these stages from DDoS perspective, it is important to understand the botnet infrastructure and how it is built.
Building up the botnet As mentioned, the distributed nature of a DDoS attack requires millions of infected machines globally. Weaponization The wide range of open source software has removed the technical barrier for creating malicious code.
It was originally developed to test the throughput of server performance; however, the Anonymous group used this open source tool to launch sophisticated DDoS attacks. It was later powered with booster scripts, which are text files that contain additional basic code, called a booster script. This booster script also allows the attacker to specify the list of target URLs to attack.
A tool called hping was developed to overcome anonymity challenges with Ion Cannon tools.
In this article

Our Blockchain Consulting Services aim at providing the based with the use case analysis answering the questions Why? We deal based three parameters: release automation, blockchain virtualization and blockchain performance management. Before an app goes live, it blockchain be deployed on the test network development test its functionalities. The blockchain company creates Web blockchain Mobile App user experiences that both clients and their customers love. Blockchain is essentially an online public ledger that development a permanent and accessible record of every stage of the supply chain. Bring ontime readymade solutions to customer doorsteps on their just one tap.
DDoS attacks
EOS accomplishes consensus by using multi-threading as well as a delegated proof-of-stake algorithm. They have their own community forum named as EOS Forum, enabling developers and investors to discuss the platform and EOS Talk for their users based on the steem blockchain.
OpenChain is an open-source distributed ledger technology, highly suited for organizations willing to manage the digital assets in a secure and scalable manner. Unlike the consensus mechanism used in Bitcoin, it uses Partionned Consensus where one instance will only have a single authority for validation of transactions.
Since there is no miner in the OpenChain, the transactions are free of costs and can be validated by the asset administrator, making it more efficient than other platforms. Founded in late , Ethereum is an open-source and blockchain based distributed computing platform proposed by Vitalk Buterin, a year old Russian-Canadian programmer. Ethereum is known for running smart contracts on a custom-built blockchain.
Every node within the network has to run an EVM implementation. Though enterprises have adopted Ethereum widely, it is essential to understand that Ethereum is a public permissionless blockchain platform , built for restricted access versus mass consumption. Moreover, it is the PoW Proof of Work based platform, which is comparatively slower in terms of speed.
But it might change its consensus algorithm to Proof of Stake in the coming years. Ether is a native cryptocurrency of Ethereum, used for fueling the Ethereum ecosystem. A developer who builds applications using Ethereum has to pay charges in Ethers, for executing transactions and running apps on the Ethereum network. Ethereum has also built a large online support community to keep everyone up-to-date with product enhancements and updates. The Ethereum Enterprise Alliance EEA is a non-profit organization with more than members, connects Fortune companies, academics, start-ups, and blockchain companies with Ethereum subject matter experts.
Morgan Chase, and Intel, who are embracing the use of the Ethereum platform. Originally developed at the Walt Disney Company in and open-sourced later in , the Dragonchain platform has been specifically designed for enterprises.
Their blockchain as a service offers flexibility to businesses by allowing them to utilize Interchain that provides the capabilities of other blockchains. With their cloud-based model for Blockchain as a Service, the need for patch implementation, updates and server setup is eliminated.
Also, the platform can support any programming language, including Python, Node. With five levels of consensus, Dragonchain offers a wide spectrum of trust and allows users to use multiple proof protocols. The role of NEO token is to generate GAS tokens which can be used to pay transaction fees to run applications on the network.
Neo uses Delegated Byzantine Fault Tolerance as its consensus algorithm. The creators of Neo selected this protocol because it allows better performance and scaling as compared to other consensus mechanisms. Since blockchain is moving at a frenetic pace of innovation, new platforms have started to emerge with additional features and new releases.
No doubt that there are plenty of blockchain platforms available across the world, enterprises need to understand the right platforms to build highly scalable applications. Therefore, we have discussed the platforms used by the top blockchain companies including IBM, Intel, Microsoft, and so on.
As one of the leading blockchain companies, we provide blockchain consultation to our clients and help them select the right blockchain platform and technology stack that meets their business needs. Once you let us know your requirement, our technical expert will schedule a call and discuss your idea in detail post sign of an NDA.
Necessary cookies are absolutely essential for the website to function properly. This category only includes cookies that ensures basic functionalities and security features of the website.
These cookies do not store any personal information. Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies.
It is mandatory to procure user consent prior to running these cookies on your website. Talk to our Consultant. Now, the question is… What is a blockchain platform? How to select a Blockchain Platform for your business? Akash Takyar. Akash is an early adopter of new technology, a passionate technology enthusiast, and an investor in AI and IoT startups.
Write to Akash. What is the development status of a platform? What type of Blockchain do you require? What Languages does the platform support?
How popular is the platform? Look at the reputation of a blockchain platform on websites like GitHub or Reddit. What Blockchain Consensus Protocol does the platform use to achieve consensus? Does the platform support Smart Contracts Functionality? What kind of scalability does your solution need? Hyperledger Fabric. Hyperledger Sawtooth. Hedera Hashgraph. The use cases are significant. The BSN claims to have already deployed more than 2, blockchain applications across enterprises and government organizations in China, in the form of over public city nodes in the country and eight nodes abroad.
CryptoSlate does not endorse any project or asset that may be mentioned or linked to in this article. Please take that into consideration when evaluating the content within this article. Disclaimer: Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. None of the information you read on CryptoSlate should be taken as investment advice, nor does CryptoSlate endorse any project that may be mentioned or linked to in this article.
Buying and trading cryptocurrencies should be considered a high-risk activity. Please do your own due diligence before taking any action related to content within this article. Finally, CryptoSlate takes no responsibility should you lose money trading cryptocurrencies. One bank seems to say so. The day is finally here—today, depends on how you cut it, the CME Group will be launching a futures market for Ethereum.
Bitcoin-focused DeFi protocol Badger joins hands with Yearn. Ethereum 2. Trending News. Close Window 🔥 Trending Coins Cardano. In a DoS attack, a threat actor uses a single machine to exhaust the target server; however, a DDoS attack is much more powerful as millions of machines can be used to exhaust a target server. More and more organizations are moving to the cloud with massive infrastructure to fulfill their immersive customer demands. Organizations either build their own heavy server infrastructure, or they move to cloud providers to host their servers.
Today, attackers prefer the DDoS attack method to disrupt target services as they can generate GBs to TBs of random data to overwhelm the target, and also it becomes difficult for a target security team to identify and block each individual attacking machine, as they are millions in number.
Furthermore, attackers never legitimately control their attacking machines, but rather they infect millions of computers worldwide with some tailored malware and then get complete access to launch a massive DDoS attack.
This collection of millions of infected computers is named a botnet and the individual infected computers are named bots. The first instance of DDoS is a bit hard to recall exactly, but the first noticeable and significant attack occurred in , and it targeted the University of Minnesota.
It impacted more than systems and brought down the entire infrastructure for several days. Dyn confirmed the Mirai botnet as a primary source of malicious attack traffic. The attack opened up an important concern on internet security and threats.
To launch a DDoS attack, a threat actor can either build the entire botnet network or rent it from a dark web marketplace. Once the attacker is ready with their weapons, they need to discover vulnerable sites or hosts, or maybe an entire network. A computer scientist at Lockheed-Martin Corporation coined a term called cyber kill chain that lays out the stages of a cyber attack, starting from reconnaissance to final goal of attack.
These stages are as follows:. In order to understand each of these stages from DDoS perspective, it is important to understand the botnet infrastructure and how it is built. As mentioned, the distributed nature of a DDoS attack requires millions of infected machines globally.
Today, attackers leverage the dark web marketplace and either rent readily available botnets or buy them. There are several tools, such as Jumper, Dirt, and Pandore, that eliminate the technical barrier in creating these botnets.
The targeted system can be as large as a data center and as small as a computer. In both cases, the development of a botnet involves identifying hosts with vulnerabilities that can be exploited with some malware families.
Attackers look for information directly or indirectly related to their target to gain unauthorized access to their protected assets. The threat actor tries all possible ways to bypass the existing security systems, such as firewalls, Intrusion Prevention System IPS , web application firewalls, and endpoint protection. The wide range of open source software has removed the technical barrier for creating malicious code. If a programmer has malicious intent and develops the code, a new breed of malware can be developed that would be difficult for security systems to detect.
Once the malicious code is developed or software purchased from the dark web marketplace, this software can either be delivered through spear phishing emails or can also be sent through spam email campaigns. The selection of either depends on the target and also the sophistication of the operation. We can classify the process into the following three groups of methods for propagating malicious code:.
The attacker's toolkit is specially designed to accept a file request from a compromised system. Unlike the central source propagation method, attackers transmit both exploit and code together into the victim machine:. Once the malware is delivered to the network, it will initiate the process of exploiting unpatched software vulnerabilities, weak software coding practices, and lack of user attention. Usually, there are numerous vulnerabilities present in the network; however, the availability of exploits makes the vulnerability much more critical in nature.
In the installation stage, the malware is installed in the targeted system and allows the remote attacker to gain access to it. During the installation process, the malware may be installed in the user space or kernel space of a system. Malware installed in the user space has a high possibility of detection; however, malware installed in the kernel space has a low chance of being detected by security systems, such as endpoint protection, endpoint detection, and response platforms.
After the weapon has been successfully installed, the target is now completely under the control of a remote central system, named the system. The network of compromised devices is called a botnet, completely under the control of the threat actor; however, the botnet remains silent until it gets activated by the attacker.
There are even several types of encrypted bot-to-bot communication present over public peer-to-peer networks. Once the C2 channel has been established, the attacker can launch the DDoS attack on the target. At this stage, the attacker runs the script to activate all the bots in the entire botnet. The attacker also configures the botnet regarding what type of traffic needs to be generated.
DDoS attacks are carried out in several ways. However, attackers select one of them based on different factors, such as target difficulty, financial capability, anonymity, priority, and other factors. It does not take much technical expertise to run the DDoS attack program and launch it. There are mainly three types of attack, categorized as follows:.
These are attack campaigns in which it is planned to consume the network resources of the target system. In this attack, network bandwidth gets completely consumed by flooding. The following are several types of flooding attacks.
UDP is a protocol embedded in the IP packet for socket-level communication between two devices.
The blockchain company has experience working with various distributed ledger technologies, including Hyperledger, Ethereum, R3Corda, and Hashgraph. Major Clients : U. The blockchain company has created an array of branded white-label products serving crowdfunding, private blockchains, and other applications.
Market, Kepler Collective. Synsoft Global is a blockchain technology company based in central India. Since , the software and blockchain development company has delivered a variety of projects for companies from one-person startups to enterprises.
The team at 10Clouds has immense expertise in blockchain technologies and has worked on numerous projects involving Ethereum, smart contracts development, and crowdsale. Inn4Science provides development process transparency and predictability by using Agile methodologies for target-setting and business analysis. The blockchain development company creates products based on Ethereum, Bitcoin, and deals with advanced development technologies such as Exonum, Node.
OpenLedger is a team of seasoned blockchain developers with vast experience. They work on custom projects for such industries as FinTech, entertainment, insurance, and many more. They provide full-cycle development solutions for enterprises and startups. The team at S-PRO creates a unique flow to turn your idea into a valuable product. Titanium Blockchain is a pioneering blockchain company that offers full-scale services in blockchain development for a range of key industries.
Look4App is a Polish software and blockchain development company that delivers cutting-edge blockchain and web development projects. With a strong FinTech background and eye for exceptional design, they deliver complex solutions on time and always strive for the best quality. They have all the qualities to become a genuine, trustworthy blockchain development partner. Major Clients : Travelplanet.
IO, Hays Poland sp. Adoriasoft is a custom software and blockchain development company that delivers stellar results. Having deep knowledge and experience in information security and cryptography, Adoriasoft main focus is distributed applications, blockchain and smart contracts projects. The blockchain company creates Web and Mobile App user experiences that both clients and their customers love. Espeo is a software house focusing on product development, design and testing. The blockchain company works with Ethereum platform, Truffle and Open Zeppelin frameworks using JavaScript and Solidity programming languages.
They are not just your typical blockchain company but rather your technical partner that guides clients towards the best technology match possible for their project. Block offers development and consultancy services focusing on blockchain technology and smart contracts. The blockchain company provides the infrastructure for Crypto and Machine Economy. Block works on blockchains such as Ethereum, Quorum, Bitcoin and Dash, and provides smart contract audits and DApp development services.
Imaginovation is an award-winning software and blockchain development company offering creative web and mobile solutions for a variety of industries. The blockchin company is at the forefront of Blockchain technology, creating multiple projects with this new approach. At Revelry the team focuses on building on innovative tech stacks and customizing their services to meet your business needs.
By partnering with the blockchain company on digital innovation and blockchain development, you collaborate to build solutions not only to create new business lines, but also grow into a tech company on your own.
Revelry combines entrepreneurial and product experience with a wealth of talent and expertise to meet your unique business goals and objectives. One bank seems to say so. The day is finally here—today, depends on how you cut it, the CME Group will be launching a futures market for Ethereum.
Bitcoin-focused DeFi protocol Badger joins hands with Yearn. Ethereum 2. Trending News. Close Window 🔥 Trending Coins Cardano. Name Changing Token. Bitcoin SV. Binance Coin. Spartan Protocol. Unifi Protocol DAO. Synthetix Network Token. Celsius Network. CME Group. Grayscale Investments. To launch a DDoS attack, a threat actor can either build the entire botnet network or rent it from a dark web marketplace.
Once the attacker is ready with their weapons, they need to discover vulnerable sites or hosts, or maybe an entire network. A computer scientist at Lockheed-Martin Corporation coined a term called cyber kill chain that lays out the stages of a cyber attack, starting from reconnaissance to final goal of attack.
These stages are as follows:. In order to understand each of these stages from DDoS perspective, it is important to understand the botnet infrastructure and how it is built.
As mentioned, the distributed nature of a DDoS attack requires millions of infected machines globally. Today, attackers leverage the dark web marketplace and either rent readily available botnets or buy them. There are several tools, such as Jumper, Dirt, and Pandore, that eliminate the technical barrier in creating these botnets. The targeted system can be as large as a data center and as small as a computer.
In both cases, the development of a botnet involves identifying hosts with vulnerabilities that can be exploited with some malware families. Attackers look for information directly or indirectly related to their target to gain unauthorized access to their protected assets.
The threat actor tries all possible ways to bypass the existing security systems, such as firewalls, Intrusion Prevention System IPS , web application firewalls, and endpoint protection. The wide range of open source software has removed the technical barrier for creating malicious code.
If a programmer has malicious intent and develops the code, a new breed of malware can be developed that would be difficult for security systems to detect.
Once the malicious code is developed or software purchased from the dark web marketplace, this software can either be delivered through spear phishing emails or can also be sent through spam email campaigns.
The selection of either depends on the target and also the sophistication of the operation. We can classify the process into the following three groups of methods for propagating malicious code:.
The attacker's toolkit is specially designed to accept a file request from a compromised system. Unlike the central source propagation method, attackers transmit both exploit and code together into the victim machine:.
Once the malware is delivered to the network, it will initiate the process of exploiting unpatched software vulnerabilities, weak software coding practices, and lack of user attention. Usually, there are numerous vulnerabilities present in the network; however, the availability of exploits makes the vulnerability much more critical in nature.
In the installation stage, the malware is installed in the targeted system and allows the remote attacker to gain access to it. During the installation process, the malware may be installed in the user space or kernel space of a system. Malware installed in the user space has a high possibility of detection; however, malware installed in the kernel space has a low chance of being detected by security systems, such as endpoint protection, endpoint detection, and response platforms.
After the weapon has been successfully installed, the target is now completely under the control of a remote central system, named the system.
The network of compromised devices is called a botnet, completely under the control of the threat actor; however, the botnet remains silent until it gets activated by the attacker. There are even several types of encrypted bot-to-bot communication present over public peer-to-peer networks. Once the C2 channel has been established, the attacker can launch the DDoS attack on the target. At this stage, the attacker runs the script to activate all the bots in the entire botnet.
The attacker also configures the botnet regarding what type of traffic needs to be generated. DDoS attacks are carried out in several ways. However, attackers select one of them based on different factors, such as target difficulty, financial capability, anonymity, priority, and other factors.
It does not take much technical expertise to run the DDoS attack program and launch it. There are mainly three types of attack, categorized as follows:. These are attack campaigns in which it is planned to consume the network resources of the target system. In this attack, network bandwidth gets completely consumed by flooding. The following are several types of flooding attacks.
UDP is a protocol embedded in the IP packet for socket-level communication between two devices. A UDP flood attack does not exploit any specific vulnerability of the target system, but rather it simply disrupts the normal traffic of the target system by overwhelming it with a high level of flooding.
It points to random ports on the target server and consumes all the traffic bandwidth for the target system. Usually, this kind of attack is considered in the class of a small-to-medium-level flood attack and measured in Mbps and PPS, as shown in the following diagram:. Again,it doesn't rely on any vulnerabilities to work. Being one of the oldest flooding techniques, organizations have practices to deploy control-plane policies over network devices to restrict the amount of ICMP packets that can processed by the control planes of devices.
IGMP is a multicast protocol, connectionless in nature. It is non-vulnerability-based, involving the sending of a large amount of IGMP message reports to networks or routers. An amplification attack takes the opportunity of a disparity between a request and a reply in a communication channel.
An attacker can compromise a router and force the router to send broadcast messages on multicast addresses by spoofing the source address. It can even be used with DNS amplification, in which the attacker can compromise a recursive DNS name server to cache large files.
